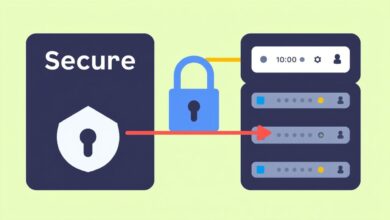
Boost Server Security: Securing Server Logins with Two-Factor Authentication (2FA)

In today’s digital landscape, server security is paramount. Your servers hold valuable data, run critical applications, and act as the backbone of your operations. Unfortunately, they are also prime targets for cyberattacks. While a strong password is a necessary first step, it is no longer sufficient on its own to protect against increasingly sophisticated threats. This is where Securing Server Logins with Two-Factor Authentication (2FA) becomes not just a best practice, but a critical necessity.
Why Passwords Alone Are a Risk
Cybercriminals employ various tactics to gain unauthorized access to servers. These include:
- Brute-Force Attacks: Automated tools repeatedly guess password combinations until successful. Weak passwords can be cracked in minutes or hours.
- Phishing and Social Engineering: Tricking users into revealing their credentials through deceptive emails or websites. (As highlighted in general internet security threats).
- Credential Stuffing: Using lists of usernames and passwords stolen from data breaches on other sites, hoping users have reused their credentials.
- Malware: Keyloggers or other malicious software (like Trojans or spyware, mentioned in the search results) designed to capture login information directly from a user’s device.
Even the strongest, most unique password can potentially be compromised through these methods. A single layer of security is simply not enough to defend against persistent attackers.
Understanding Two-Factor Authentication (2FA)
Two-Factor Authentication (2FA), often a component of Multi-Factor Authentication (MFA), adds an extra layer of security beyond just a username and password. It requires the user to provide *two or more* distinct forms of verification from different categories before access is granted. These categories typically include:
- Something You Know: This is your password or PIN.
- Something You Have: This could be a physical token, a smartphone receiving a code via an app (like Microsoft Authenticator), or a hardware security key.
- Something You Are: This is biometric data, such as a fingerprint or facial scan.
By requiring authentication from at least two of these categories, 2FA significantly reduces the risk of unauthorized access, even if one factor (like your password) is compromised.
[Hint: Insert image/video illustrating the 2FA login process]How 2FA Secures Server Logins
Implementing 2FA for server logins, such as RDP (Remote Desktop Protocol) or console access, means that after a user enters their correct username and password, they are prompted for a second verification step. This could involve:
- Entering a time-sensitive code generated by an authenticator app on their smartphone.
- Responding to a push notification sent to a registered device.
- Inserting a physical security key.
For environments leveraging solutions like Windows Server and Active Directory, 2FA solutions can often integrate seamlessly, making the implementation process smoother. The summary provided specifically mentions the need to integrate 2FA within environments like Active Directory and the use of existing authentication apps like Microsoft Authenticator, highlighting the practical application of this technology for Windows environments.
This additional step, requiring physical possession of a device or biometric data, makes it exponentially harder for attackers using stolen credentials or automated tools to gain access. They might have the password, but they won’t have the second factor.
Key Benefits of Implementing 2FA on Servers
Deploying 2FA for server logins offers substantial security advantages:
- Stronger Defense Against Credential Theft: If a password is leaked or guessed, the second factor acts as a critical barrier.
- Mitigation of Phishing and Social Engineering: Even if a user falls for a phishing scam and gives up their password, the attacker still can’t log in without the second factor.
- Protection Against Brute-Force Attacks: Automated attacks are rendered ineffective because the attacker cannot provide the dynamic second factor.
- Compliance Requirements: Many industry regulations and security standards now mandate the use of multi-factor authentication for accessing sensitive systems, including servers.
- Reduced Risk of Data Breaches: Unauthorized server access is a primary cause of data breaches. 2FA significantly lowers this risk.
While physical security (like locking the server room, which could technically be considered a form of physical authentication for physical access) is important, the focus for server logins is on bolstering the digital access point, as noted in the summary information. Adding a digital second factor directly to the software login process is key.
[Hint: Insert image/video showing different types of 2FA methods]Implementing 2FA: Considerations
Integrating 2FA into your server login process requires careful planning. You’ll need to choose a 2FA solution that is compatible with your server operating system (e.g., Windows Server RDP, Linux SSH) and potentially your existing identity management system (like Active Directory). Consider the user experience – while security is paramount, the method chosen should be as convenient as possible for legitimate users to encourage adoption and minimize frustration. Look for solutions that offer reliable methods like mobile authenticator apps or hardware tokens.
Implementing 2FA can be done either during the initial login phase or as a requirement for accessing specific high-value resources after the initial login, depending on the solution and your security policies.
Beyond Two Factors: Multi-Factor Authentication (MFA)
While 2FA is a significant improvement, Multi-Factor Authentication (MFA) simply means using *two or more* factors. This could involve three or more distinct verification methods for even higher security, although 2FA is often the most practical and impactful starting point for securing server logins.
Conclusion
In an era of escalating cyber threats, relying solely on passwords for server access is a gamble you cannot afford to take. Securing Server Logins with Two-Factor Authentication (2FA) is a fundamental security measure that provides a robust defense against common attack vectors like brute force, phishing, and credential theft. By requiring users to prove their identity through multiple distinct factors, you drastically reduce the likelihood of unauthorized access, protecting your critical assets and data. Implement 2FA today to significantly strengthen your server security posture.
For more tips on strengthening your defenses, read our article on Best Practices for Strong Server Passwords and User Authentication.
To learn more about the broader landscape of cybersecurity threats and defenses, you can explore resources like the CISA website on Multi-Factor Authentication.