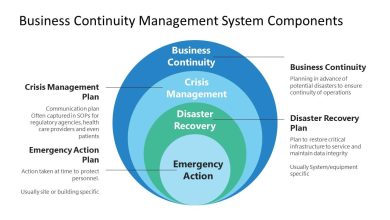
Establishing a Secure Wi-Fi Network: A Step-by-Step Guide
Okay, here’s a thorough outline adn a long-form article about establishing a secure Wi-Fi network, written in the style you requested.
Outline
| # | Heading | Subheading | LSI Keywords |
| :– | :————————————————————- | :————————————————————————————————– | :————————————————————————————————————- |
| 1 | Initial considerations for Home Network Protection | The Importance of Wireless Security in Today’s Digital Age | wireless network security, home network safety, internet security protocols |
| 2 | | Understanding the Risks of an Unprotected Network | open Wi-Fi risks, unsecured network vulnerabilities, Wi-Fi hacking threats |
| 3 | | Identifying Yoru Current Network Setup: A Preliminary Audit | network configuration check, Wi-Fi setup assessment, current security measures evaluation |
| 4 | Router Configuration: The Foundation of Network Fortification | Accessing Your Router’s Administrative Interface | router login, router admin panel, accessing router settings |
| 5 | | Changing the Default Router Login Credentials: Your First Line of Defense | default username password change, router password security, strengthening router access |
| 6 | | Updating Router Firmware: Keeping Your Network’s Gatekeeper Up-to-Date | router firmware update, latest router software, router security patches |
| 7 | Wireless Network Security Protocols: Choosing the Right Shield | Differentiating Between WEP, WPA, WPA2, and WPA3: A Comparative Analysis | Wi-Fi encryption types, WPA vs WPA2 vs WPA3, wireless security standards |
| 8 | | Implementing WPA3: The Gold Standard in Wireless Security | WPA3 deployment, enabling WPA3, WPA3 configuration |
| 9 | | The Case for WPA2 in Mixed-Mode Environments: Balancing Compatibility and Security | WPA2 mixed mode, WPA2 compatibility, WPA2 security features |
| 10 | SSID Management: Concealing Your Network from Prying Eyes | Deciding Whether to Broadcast Your SSID: Visibility vs. Security | SSID broadcast, hiding SSID, network visibility |
| 11 | | Crafting a Strong, Unique SSID: Avoiding Common Pitfalls | unique SSID, strong SSID name, SSID naming conventions |
| 12 | | The SSID Cloaking Myth: why Hiding your SSID Isn’t Foolproof | SSID cloaking limitations, hidden network fallacies, SSID security myths |
| 13 | Password Strength: The Key to Impenetrable Wi-Fi | The Anatomy of a Strong Wi-fi Password: Length, Complexity, and Uniqueness | strong Wi-Fi password, Wi-Fi password complexity, password length recommendations |
| 14 | | Employing a Password manager: generating and Storing Complex Passwords with Ease | password manager benefits, secure password storage, generating random passwords |
| 15 | | Password Rotation: A Habit for Enhanced Security | regular password changes, Wi-Fi password rotation, password update frequency |
| 16 | Advanced Router Settings: tightening the Network’s Defenses | Enabling MAC Address Filtering: Restricting Access to Authorized Devices | MAC address filtering, device access control, whitelisting devices |
| 17 | | Configuring the Router’s Firewall: an Additional Layer of Protection | router firewall settings, enabling router firewall, firewall configuration |
| 18 | | Disabling Remote Management: Limiting Accessibility to Your Router | disable remote access, router remote management, local network access |
| 19 | Guest Networks: Isolating Visitors for Enhanced Security | Why a Separate Network for Guests is Crucial for Home Security | guest network benefits, isolating guest traffic, home network segregation |
| 20 | | Setting Up a Guest Network: A Step-by-Step Guide | creating guest network, guest Wi-Fi setup, guest network configuration |
| 21 | | Customizing Guest Network Settings: Balancing Convenience and Security | guest network restrictions, guest Wi-Fi password, guest network access |
| 22 | Network Monitoring and Maintenance: Staying One Step Ahead | Regularly Reviewing Connected devices: identifying Intruders | connected devices list, network monitoring tools, detecting unauthorized access |
| 23 | | Utilizing Network Monitoring Software: Tools for Real-time Security Insights | Wi-Fi monitoring software, network security analysis, real-time network monitoring |
| 24 | | Responding to Security Breaches: A Plan of Action | security breach response, Wi-Fi security incident, network intrusion recovery |
| 25 | Beyond the Router: Additional Measures for Network Security | Implementing a VPN for secure Browsing: Protecting Your Online Activities | VPN for home network, secure Wi-Fi browsing, online privacy protection |
| 26 | | Educating Household Members on Safe Wi-Fi Practices: A Collective Responsibility | Wi-Fi security awareness, safe internet habits, family internet safety |
| 27 | | Staying Informed About the Latest Security Threats: A Proactive Approach | cybersecurity news, Wi-Fi security updates, latest network threats |
| 28 | Conclusion: Forging Ahead with confidence | Reinforcing the Pillars of Your Wi-Fi Security | Wi-Fi security best practices, maintaining network security, strengthening wireless protection |
Article: Establishing a Secure Wi-Fi Network: A Step-by-Step Guide
Initial Considerations for Home Network protection
%%Portuguese%%
in today’s hyper-connected world, our reliance on the internet has reached unparalleled heights. From streaming our favorite shows to managing our finances, the internet is, well, the backbone of our daily routines. At the heart of this connectivity lies our home Wi-Fi network,the unsung hero that seamlessly links our devices to the vast expanse of the digital realm. But, you see, with this increased reliance comes a growing need to safeguard our online presence.Ensuring the security of our Wi-Fi network is no longer an option; it’s a necessity.
Think of your Wi-Fi network as the front door to your digital home. An unsecured network is like leaving that door wide open, inviting unwanted guests to waltz in and rifle through your personal belongings. The risks are real and can range from someone casually piggybacking on your internet connection to more malicious actors stealing sensitive details or even launching cyberattacks from your network. Who would want that on their conscience? In this digital age, protecting our Wi-Fi networks is important for maintaining our privacy, protecting our data, and ensuring a safe online experience for everyone in our household. It is indeed similar to locking your doors at night.
to establish a secure Wi-Fi, the very first step involves understanding the lay of the land. What kind of network setup do you currently have? What security measures are, if any, already in place? Taking stock of your current setup is like assessing the foundation of a house before starting a renovation. The first step might be to make a list of all the devices connected to your network. A complete network is like a complex machine with many moving parts, so it requires attention to detail. You have to identify your router’s make and model, check the type of encryption protocol your network is using (e.g.,WPA2,WPA3),and determine whether your router’s firmware is up to date. This initial audit will provide a clear picture of your network’s strengths and weaknesses, allowing you to make informed decisions as you embark on the journey of fortifying your digital defenses.Don’t just jump in blind; take the time to understand your current network habitat.
Router configuration: The Foundation of network Fortification
%%Spanish%%
Alright, let’s roll up our sleeves and dive into the nitty-gritty of router configuration. Your router is basically the gatekeeper of your home network. It’s the central hub that manages all incoming and outgoing internet traffic. naturally, securing your router is paramount to establishing a robust security perimeter. It’s like adding a sturdy lock to your front door, making it considerably harder for unwanted guests to gain entry.
First things first, you need to access your router’s administrative interface. This is where all the magic happens, where you can tweak settings and customize your network to your heart’s content. typically, you can access this interface by entering your router’s IP address into a web browser. if you are wondering “It is the same as typing a website address.” you are right! The default IP address is often something like 192.168.1.1 or 192.168.0.1, but it can vary depending on your router’s make and model. Your router’s manual or the manufacturer’s website should provide the specific IP