Key Factors When Choosing Your Server Backup Strategy
In today’s digital landscape, data is the lifeblood of almost every organization. Servers house critical business applications, customer databases, intellectual property, and essential operational data. Losing this data, even temporarily, can lead to significant financial losses, irreparable damage to reputation, and potential legal liabilities. This is why a robust and well-thought-out server backup strategy is not just a best practice; it’s a fundamental necessity for business continuity and resilience.
Simply having backups isn’t enough. The effectiveness of your backup plan hinges on several key factors that must be carefully considered. Choosing the right approach involves more than just picking software; it requires understanding your specific needs, assessing risks, and planning for various scenarios, including IT disaster recovery. Let’s dive into the critical elements you need to evaluate when developing your server backup strategy.
Why Your Server Backup Strategy is Non-Negotiable
Data loss can stem from numerous causes: hardware failure, human error, cyberattacks like ransomware, natural disasters, or even software corruption. Without a reliable server backup strategy, any of these events could cripple your operations. A good strategy ensures you can quickly recover data and systems, minimizing downtime and getting back to business as usual.
Beyond simple recovery, a strong strategy is vital for:
- Meeting compliance requirements (e.g., GDPR, HIPAA, SOX) that mandate data retention, privacy, and recovery capabilities.
- Protecting against evolving cybersecurity threats.
- Ensuring business continuity in the face of unforeseen disruptions.
According to various industry reports, a significant percentage of businesses that suffer major data loss never fully recover. This underscores the importance of proactive planning.
[Hint: Insert image/video illustrating data loss risks or backup process flow here]Key Factors When Choosing Your Server Backup Strategy
Developing an effective strategy requires taking into account several crucial considerations. Here are the primary factors:
1. Identifying Your Critical Data
Before you back up anything, you need to know *what* is essential. Not all data has the same value or requires the same level of protection. Identify:
- Business-critical applications and databases.
- Sensitive customer or employee information.
- Intellectual property and proprietary data.
- Operating system and application configurations necessary for system recovery.
- User files and documents.
Prioritizing data helps you allocate resources effectively and define different backup tiers based on importance.
2. Recovery Time Objective (RTO) and Recovery Point Objective (RPO)
These are arguably the most critical metrics defining your server backup strategy. They determine how quickly you need to recover and how much data you can afford to lose.
- Recovery Time Objective (RTO): This is the maximum acceptable downtime for a system or application after a failure. If your email server can only be down for 1 hour, your RTO for email is 1 hour.
- Recovery Point Objective (RPO): This is the maximum acceptable amount of data loss, measured in time. If you can only afford to lose 15 minutes of data from your CRM database, your RPO for the CRM is 15 minutes.
Setting realistic RTOs and RPOs for different data types and systems is fundamental. Tighter RTOs and RPOs typically require more advanced, frequent, and potentially more expensive backup and recovery solutions.
3. Backup Frequency and Schedule
How often should you back up? This ties directly into your RPO. To meet a 15-minute RPO, you might need continuous replication or backups running every few minutes. For less critical data with a higher RPO (e.g., 24 hours), daily backups might suffice. Your schedule should also consider when systems are least busy to minimize performance impact.
Automatic backup scheduling is a key feature to ensure consistency and reliability.
4. Budget and Cost Considerations
Your budget will significantly influence the technologies and methods you can employ. Costs include:
- Backup software licensing.
- Backup hardware (servers, storage devices, tapes).
- Off-site storage costs (cloud subscriptions, physical storage).
- Network infrastructure required for data transfer.
- Personnel time for management and testing.
Balance the cost of implementing and maintaining the strategy against the potential cost of data loss and downtime.
5. Storage Location and The 3-2-1 Rule
Where will you store your backups? Relying solely on on-site backups leaves you vulnerable to site-wide disasters like fire or flood. A crucial principle is the 3-2-1 Backup Rule:
- Have at least 3 copies of your data.
- Store the copies on at least 2 different types of storage media (e.g., disk and tape, or disk and cloud).
- Keep at least 1 copy off-site.
Off-site storage options include cloud backup services, a secondary data center, or physically transporting media to a secure remote location. Using multiple destinations enhances the resilience of your overall system.
6. Security and Encryption
Backups are valuable data. They must be protected from unauthorized access and cyber threats, especially ransomware, which targets backup files. Key security measures include:
- Encrypting data at rest (on storage media) and in transit (during transfer).
- Using strong access controls and separate credentials for backup systems.
- Implementing air-gapped or immutable backups where possible to prevent ransomware from encrypting backups.
Compliance regulations often mandate specific encryption standards and security protocols for stored data.
7. Backup Technology and Methods
Various backup technologies and methods are available, each with pros and cons:
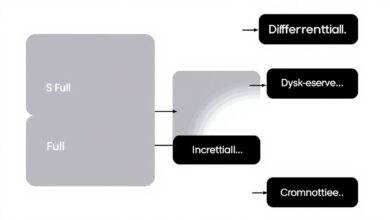
- Full Backups: Copying all selected data. Simple but time-consuming and requires significant storage.
- Incremental Backups: Copying only data that has changed since the last backup (full or incremental). Faster and uses less space, but recovery can be complex.
- Differential Backups: Copying data that has changed since the last *full* backup. Faster than full, easier recovery than incremental.
- Disk Imaging: Creating a complete image of a server’s hard drive(s). Useful for bare-metal recovery.
Many modern solutions combine these methods (e.g., forever incremental) and incorporate features like data deduplication to reduce storage needs. Your choice depends on RTO, RPO, budget, and existing infrastructure.
8. Scalability and Resilience
Your backup solution should be able to grow with your data volume and infrastructure. It should also be resilient enough to handle failures within the backup system itself.
9. Testing Your Backups
A backup is worthless if you cannot restore from it. Regularly testing your backups is non-negotiable. Schedule periodic restore drills to verify that data can be recovered accurately and within your defined RTOs. Many organizations overlook this crucial step.
[Hint: Insert image/video demonstrating a backup restore process here]Implementing and Managing Your Strategy
Once you’ve considered these factors, choose appropriate backup technologies and solutions (on-premises, cloud, or hybrid). Implement automatic scheduling, versioning, and retention policies based on your RPOs and compliance needs.
Effective backup management is an ongoing process. It requires monitoring backup jobs, reviewing logs, and periodically reassessing your strategy as your business needs and data change.
Conclusion
A robust server backup strategy is the cornerstone of data protection and business continuity. By carefully evaluating key factors like RTO, RPO, budget, security, storage location (following the 3-2-1 rule), and backup technology, you can build a strategy that safeguards your critical data against loss and ensures you can recover quickly when disaster strikes. Don’t wait until it’s too late – planning your server backup strategy is an investment in the future and stability of your organization.
For more on why backups are essential, check out our article: Why Server Backups are Crucial and How Often to Do Them.