Understanding Key Networking Protocols: HTTP, HTTPS, FTP, and SMTP

Okay, here’s a comprehensive article outline and a detailed long-form article on the topic “Understanding Key Networking Protocols: HTTP, HTTPS, FTP, and SMTP,” following your specific guidelines.
Article Outline
| # | Outline Headings & Subheadings | LSI Keywords |
|—|—————————————————————————————————|————————————————————————————–|
| 1 | The Foundation of digital Communication | Internet protocols, network communication, data transmission |
| 2 | Decoding the Language of the Web | Web protocols, client-server model, resource transfer |
| 3 | The Unsung heroes of Data Exchange | File sharing, email communication, application-layer protocols, protocol suite |
| 4 | HTTP: The Workhorse of the World Wide Web | Hypertext transfer protocol, web browsing, stateless protocol |
| 5 | How HTTP Makes Websites Work | request-response cycle, HTTP methods, URLs, uniform resource locator |
| 6 | Inside an HTTP Request | Headers, body, status codes, request methods |
| 7 | Understanding HTTP Response Messages | Status line, headers, message body |
| 8 | The Stateless Nature of HTTP and Its Implications | Session management, cookies, persistent connections |
| 9 | HTTPS: securing the Web with Encryption | Secure Hypertext Transfer Protocol, SSL/TLS, data encryption, website security |
| 10 | The Role of SSL/TLS in HTTPS | Cryptographic protocols, digital certificates, handshake process, connection encryption |
| 11 | How HTTPS Protects Your Data | Confidentiality, integrity, authentication, secure data transfer |
| 12 | The importance of HTTPS for E-commerce and Online Banking | Secure transactions, protecting sensitive data, payment gateways |
| 13 | FTP: The File Transfer Veteran | File Transfer Protocol, file uploading, file downloading, client-server file transfer |
| 14 | How FTP Facilitates File Sharing | FTP commands, data connection, control connection, file transfer modes |
| 15 | Active vs. Passive FTP: Understanding the Differences | Port mode, passive mode, firewall considerations, establishing connections |
| 16 | Security Concerns with FTP and Secure Alternatives | Plaintext transmission, SFTP, FTPS, secure file transfer methods |
| 17 | SMTP: The Mailman of the Internet | Simple Mail Transfer Protocol, email delivery, outgoing mail server |
| 18 | The Journey of an Email: From Sender too Recipient | Mail user agent, mail transfer agent, message queue, email relay |
| 19 | SMTP Commands and Responses | SMTP verbs, status codes, email transaction, mail server communication |
| 20 | The Role of SMTP in Email Infrastructure | Mail servers, DNS, MX records, email routing |
| 21 | Beyond the Basics: Enhancing Email with Extensions | ESMTP, authentication, encryption, spam filtering |
| 22 | Protocol Interplay: How They Work Together | Webmail, email clients, file sharing on websites, integrated services |
| 23 | Common Use Cases and Scenarios | Web browsing, online shopping, file backups, sending newsletters |
| 24 | Troubleshooting Common Protocol-Related Issues | Connection errors, security warnings, email delivery problems, blocked ports |
| 25 | The Future of Networking Protocols | HTTP/3, QUIC, evolving security standards, advancements in data transfer |
The Article
The Foundation of Digital Communication
Well, picture this: the internet, a vast, interconnected web of facts, constantly humming with activity. But have you ever stopped to wonder, how it is indeed even possible for us to do the things we love, such as watching videos, sending emails, or shopping online? Well! The answer lies in the intricate set of rules that govern how data travels across this digital landscape, and these rules are known as network protocols. these protocols provide a common language for devices to communicate, ensuring that data, whether it’s a webpage, a file, or an email, reaches its intended destination reliably and efficiently.Think of them as the unsung heroes working behind the scenes, orchestrating the seamless flow of information that powers our digital world.
Without these rules, chaos would reign. Data packets could lose thier way and get corrupted, or even reach unintended destinations, a total disaster. Networking protocols prevent this potential pandemonium, thereby guaranteeing smooth and efficient communication.These protocols define everything from the format of data packets to the routes they take and the error-checking mechanisms that ensure their integrity.
They act as the traffic cops of the internet, directing the flow of information and preventing collisions. They establish the rules of engagement for devices, ensuring they can understand each other and exchange data in an organized manner. Furthermore, these protocols are the foundation upon which the entire internet is built. They are the bedrock of our online experiences, enabling everything from casual web browsing to complex financial transactions. Understanding these protocols is akin to understanding the DNA of the digital world, it gives you great insights into how the online universe actually functions. They are the silent guardians of our online interactions, working tirelessly in the background to ensure that our digital lives are connected, secure, and efficient. In other words, they are the key in unlocking the secrets behind the way we all experience and interact with the Digital world.
Decoding the Language of the Web
now, let’s dive deeper into the world of network protocols. The internet, as we certainly know it, relies on a collection of these protocols, each designed for a specific purpose. Among the most important are HTTP,HTTPS,FTP,and SMTP. These four are fundamental to our everyday online experiences,each playing a crucial role in ensuring that we can access websites,transfer files,and send emails. In other words, these protocols are the building blocks of the modern internet.
HTTP, or Hypertext Transfer protocol, is the backbone of the World Wide Web. It’s the protocol that allows web browsers to communicate with web servers, requesting and receiving web pages, images, and other resources. Think of it as the language that allows your computer to ask a website for information and get it back. It is the protocol that makes it all possible!
HTTPS, or Secure Hypertext Transfer Protocol, is the secure version of HTTP.It adds a layer of encryption to the communication, protecting sensitive data like passwords and credit card information from being intercepted. Imagine it as sending a letter in a sealed, tamper-proof envelope, rather than on a postcard.
FTP, or File Transfer Protocol, is used for transferring files between computers. It’s like having a direct line for sending and receiving files, often used for uploading websites to servers or downloading large files. In other words, this is how we get files from one place to another on the internet.
SMTP,or Simple mail Transfer Protocol,is the protocol that handles email delivery. It’s sort of like the postal service of the internet, ensuring that your emails reach their intended recipients.
These four protocols, while distinct in their functions, often work together to create a seamless online experience. as an example, when you visit a secure website, your browser uses HTTPS to communicate with the server, but if you download a file from that site, FTP might be used in the background. And when you send an email through a webmail service, SMTP and HTTP often play hand in hand.
The Unsung Heroes of Data Exchange
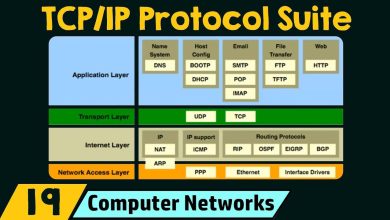
So,we’ve touched upon the individual roles of these protocols,but it is indeed crucial to understand that they are part of a larger family known as the Internet Protocol Suite,frequently enough referred to as TCP/IP. This suite is a conceptual model and set of communications protocols used on the Internet and similar computer networks. It’s like the complete rulebook for how devices should communicate online. The concept of TCP/IP can be a bit complex to grasp at first, but try to think of it as a well-organized team where each member has a specific role to play, and together, they ensure that the entire system functions smoothly.
Within this suite, HTTP, HTTPS, FTP, and SMTP reside at the application layer. This means they are responsible for providing services directly to the applications we use, such as web browsers and email clients. They are like the front-line workers of the internet, interacting directly with the software we use every day. In contrast, TCP (Transmission Control Protocol) and IP (Internet Protocol) reside at lower layers of the protocol stack. TCP is responsible for ensuring reliable, ordered, and error-checked delivery of data between applications. It’s like the quality control manager, making sure everything arrives in the correct order and without mistakes. IP, on the other hand, is responsible for addressing and routing data packets across the network. It’s like the delivery driver, making sure the packets get to the right address.
These protocols work in concert, each fulfilling its specific role to ensure that data is transmitted accurately and efficiently across the vast expanse of the internet. The beauty of this system is that each protocol can be updated and improved without affecting the others, allowing the internet to evolve and adapt to new technologies and demands.
But believe you me,just knowing that these protocols exist isn’t enough