Unlock Server Insights: A Comprehensive Guide to Managing Windows Server Event Logs Effectively
In the complex world of IT infrastructure, effectively managing Windows Server event logs is not just a best practice; it’s a fundamental necessity. These logs are the digital breadcrumbs left by the operating system and applications, providing invaluable insights into system health, security posture, and operational performance. Without proper management, you’re flying blind, potentially missing critical security threats or struggling to diagnose crippling performance issues. This guide dives deep into the strategies and techniques required for managing Windows Server event logs effectively, ensuring your systems remain secure, stable, and compliant.
Understanding the ‘why’ behind meticulous log management sets the stage. Event logs are critical for:
- Security Monitoring: Detecting unauthorized access attempts, malware activity, policy changes, and other security incidents relies heavily on analyzing security logs.
- Troubleshooting: When applications crash or services fail, system and application logs often hold the key to understanding the root cause, significantly reducing downtime.
- Compliance & Auditing: Many regulatory frameworks (like HIPAA, SOX, PCI-DSS) mandate the collection, retention, and review of specific event logs to ensure accountability and traceability.
Core Strategies for Managing Windows Server Event Logs
Effective management involves several key activities. Let’s break down the essential strategies you need to implement.
1. Consistent Monitoring and Review
Regularly checking event logs is the first step. Don’t wait for something to break. Proactive monitoring allows you to spot anomalies or warnings before they escalate into major problems. Key tools include:
- Event Viewer: The built-in Windows tool for viewing logs. Familiarize yourself with its filtering and custom view capabilities.
- Server Manager & Windows Admin Center (WAC): Offer integrated views for managing event logs across multiple servers, particularly useful in modern environments.
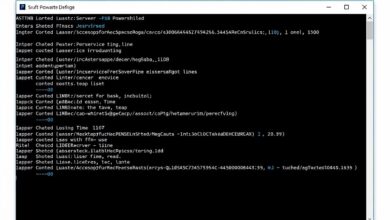
- PowerShell: For advanced users, cmdlets like
Get-WinEventprovide powerful scripting capabilities for querying and filtering logs across numerous machines. For example:Get-WinEvent -FilterHashtable @{LogName='Security'; ID=4624} -MaxEvents 10fetches the last 10 successful logon events.
2. Smart Configuration and Filtering
Default log settings are often insufficient. You need to configure logging policies to capture the right information without overwhelming your storage or analysis capabilities.
- Log Size and Retention: Define maximum log sizes and what happens when they are full (overwrite oldest events, archive, or stop logging). Archiving is often preferred for compliance. Configure these via Group Policy Objects (GPOs) for consistency.
- Audit Policies: Configure advanced audit policies (also via GPO) to specify precisely which events (e.g., logon successes/failures, object access, process creation) should be logged. Be granular to avoid excessive noise.
- Custom Views: Within Event Viewer, create custom views that filter logs based on level (Critical, Error, Warning), log source, Event ID, or keywords. This helps focus on the most important events quickly.
- Event Subscriptions: Set up subscriptions to forward specific events from multiple source computers (clients or servers) to a central collector server. This is a core component of centralized logging.
3. Centralized Log Management
Managing logs on individual servers doesn’t scale. Centralizing logs from multiple systems into a single repository offers significant advantages:
- Holistic View: Correlate events across different servers to understand complex issues or track attack paths.
- Efficient Analysis: Use powerful analysis tools on the aggregated data.
- Simplified Retention & Archiving: Manage storage and compliance requirements from one place.
Windows Event Forwarding (WEF) is a built-in, agentless mechanism to achieve this. Configure collector servers and use GPOs to push subscription settings to source computers. Alternatively, integrate logs with Security Information and Event Management (SIEM) platforms (like Splunk, QRadar, Microsoft Sentinel) for advanced correlation, alerting, and reporting capabilities.
[Hint: Insert diagram illustrating centralized logging with WEF and SIEM integration here]4. Effective Analysis and Auditing
Collecting logs is only half the battle; extracting meaningful information is key. This involves:
- Understanding Event IDs: Learn the meaning of common and critical Event IDs relevant to your environment (e.g., logon failures – 4625, software installation – 11707, service crashes – 7034). Resources like Microsoft documentation and community sites are valuable here.
- Correlation: Look for patterns or related events occurring around the same time across different logs or systems.
- Baseline Establishment: Understand what “normal” looks like in your logs to better identify deviations that might indicate problems.
- Regular Audits: Periodically perform deep dives into logs, specifically looking for security concerns or compliance deviations, not just troubleshooting immediate issues.
5. Log Maintenance: Rotation and Archiving
Event logs can grow rapidly, consuming significant disk space. Implement a clear maintenance strategy:
- Rotation/Overwriting: Configure logs to automatically overwrite the oldest events when the maximum size is reached. Suitable for less critical logs where historical data isn’t paramount.
- Archiving: Set up automatic archiving before overwriting occurs. This preserves historical log data for compliance and forensic analysis. Ensure archives are stored securely and are easily accessible when needed.
Regularly review disk space usage dedicated to logs and archives, adjusting size limits and retention policies as needed.
Bringing It All Together: Best Practices Summary
To effectively manage your Windows Server event logs:
- Define Clear Policies: Establish documented policies for logging levels, retention, and review frequency.
- Leverage Centralization: Implement WEF or a SIEM solution.
- Configure Granular Auditing: Log what you need, not everything.
- Use Filters and Custom Views: Focus your attention efficiently.
- Automate Where Possible: Use scripting (PowerShell) or dedicated tools for monitoring and alerting.
- Train Your Team: Ensure administrators understand log formats, critical event IDs, and analysis techniques.
- Regularly Review & Adapt: Periodically revisit your logging strategy to ensure it still meets your security, operational, and compliance needs.
Mastering the art of managing Windows Server event logs transforms them from a passive data store into an active intelligence source. By implementing these strategies, you enhance security visibility, accelerate troubleshooting, meet compliance requirements, and gain deeper operational insights into your Windows Server environment. Don’t underestimate the power hidden within your event logs; harness it effectively. For further reading on specific event IDs and logging mechanisms, consult the official Microsoft Event Logging documentation. Explore related topics like Windows Server Security Best Practices for a broader security context.